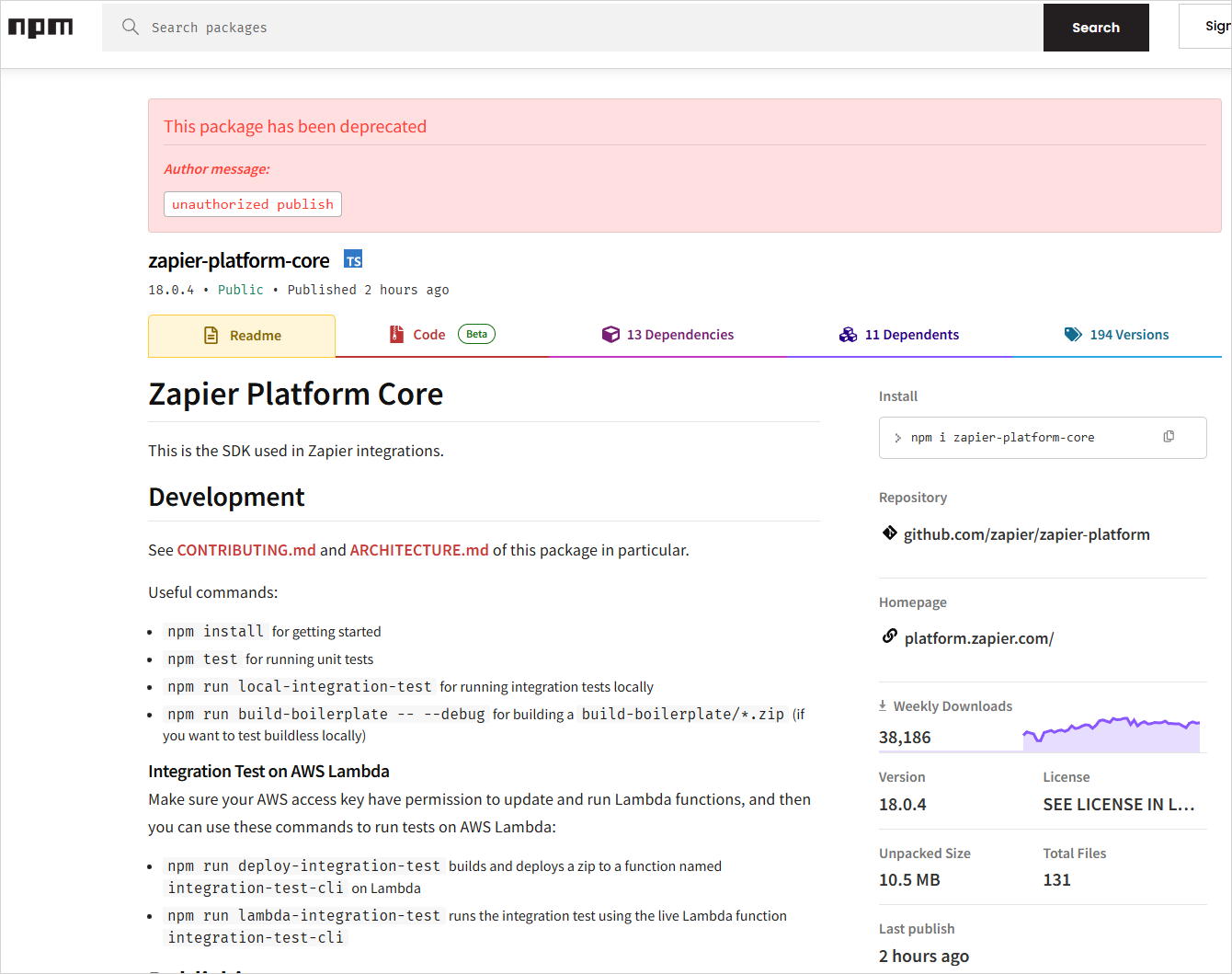
Hundreds of trojanized versions of well-known packages such as Zapier, ENS Domains, PostHog, and Postman have been planted in the npmregistry in a new Shai-Hulud supply-chain campaign.
The malicious packages have been added to NPM (Node Package Manager) over the weekend to steal developer and continuous integration and continuous delivery (CI/CD) secrets. The data is automatically posted on GitHub in encoded form.
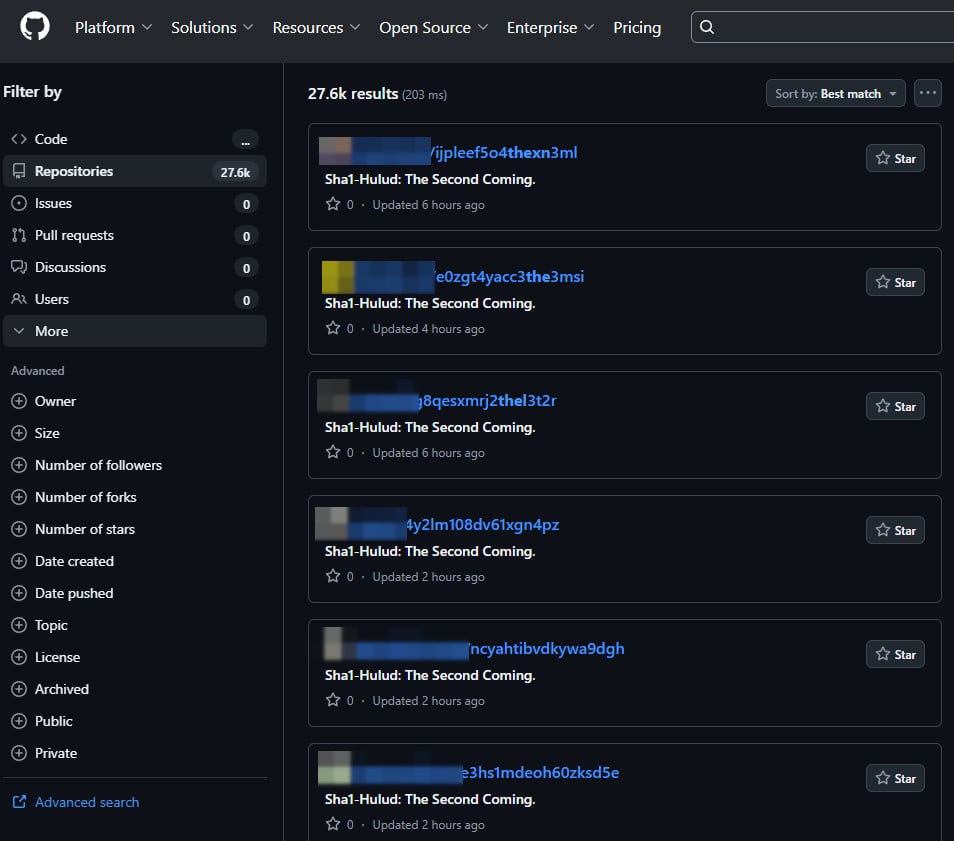
At publishing time, GitHub returned 27,600 results corresponding to entries related to the recent attack.

 compromised187 packages with a self-propagating payload that used the TruffleHog tool to steal developer secrets.
compromised187 packages with a self-propagating payload that used the TruffleHog tool to steal developer secrets.
The threat actor automatically downloadedlegitimate packages, modified the package.json file to inject a malicious script, and then published them on npm using compromised maintainer accounts.
When Charlie Eriksen, malware researcherat developer-focused security platform Aikido Security,discovered the new campaign earlier today, there were 105 trojanized packages with Shai-Hulud indicators. Since then, the number grew to 492, some of them with multiple versions.
Later, the researcher warned that the secrets stolen in the supply-chain attackwere leaked on GitHub.
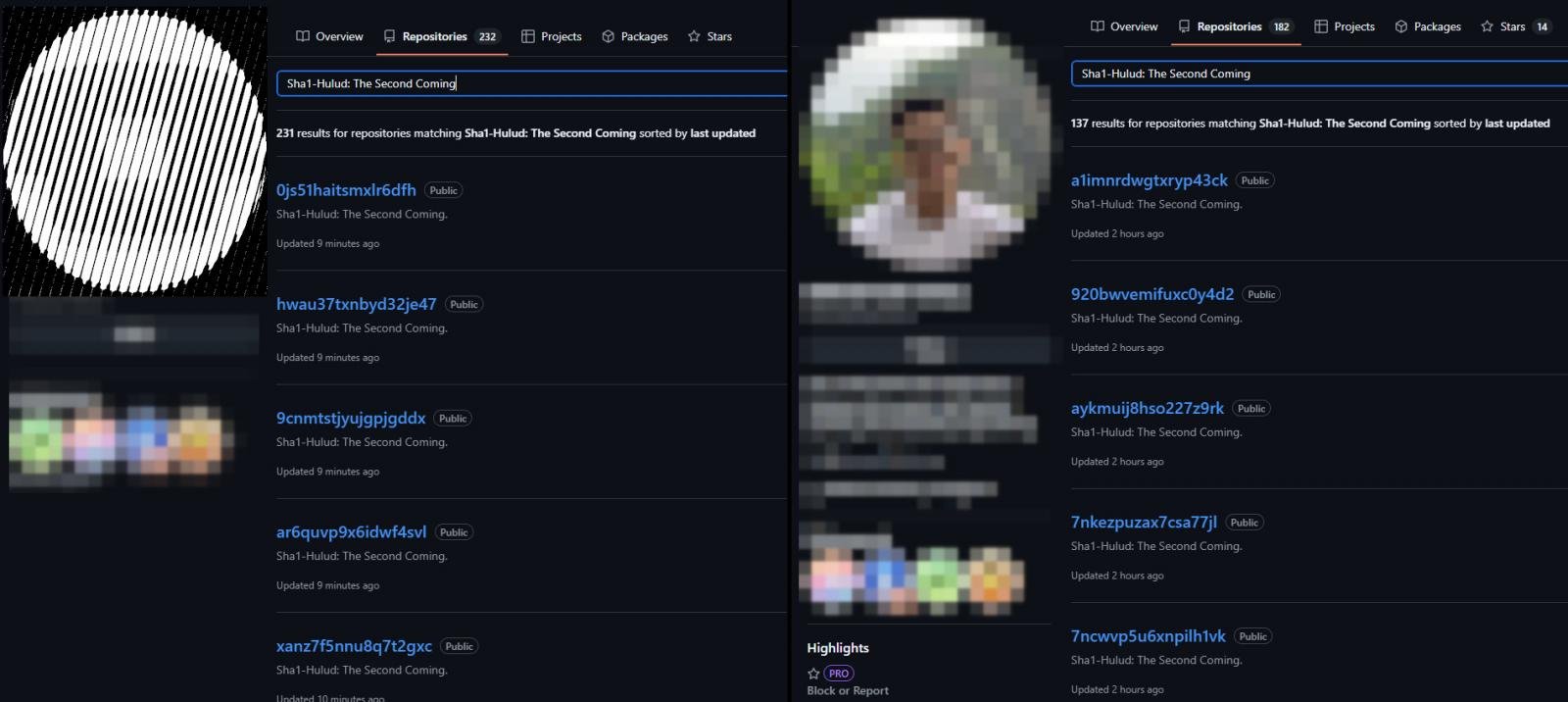
However, the campaign has grown exponentially to more than 27,000 malicious packages. Threat researchers at Wiz cloud security platform discovered around 350 unique maintaineraccounts used in the campaign, noting that “1,000 new repositories are being added consistently every 30 minutes in the last couple of hours.”
Eriksen clarified for BleepingComputer that the repositories on GitHub are indicative of compromised developers that used trojanized npm packages and thad GitHub credentials on their environment.
A technical analysis of the new Shai-Hulud malware analysis from CI/CD security company Step Security explains that thenew payloads are present in two files, one beingsetup_bun.js – a dropper disguised as aBun installer.
The second file is calledbun_environment.js and is sizeable at10MB. It relies on”extreme obfuscation techniques,” Step Security says, such as a large hex-encoded string with thousands of entries, an anti-analysis loop, and an obfuscated function to retrieve every string in the code.
According to Wiz, the malicious codecollects developer and CI/CD secrets and publishes them to GitHub repositories “with names referencing Shai-Hulud.” The malicious codeexecutes only during the pre-install stage and creates the following files:
- cloud.json
- contents.json
- environment.json
- truffleSecrets.json
Stolen secrets are published on GitHub to automatically-generated repositories that have the description “Sha1-Hulud: The Second Coming.”
It appears that the threat actor has also gained access to GitHub accounts that they are now using to create repositories with the four files above.
 introduced additional security measures to prevent supply-chain attacks on npm, following a series of high-impact attacks on the platform.However, the measures are being implemented gradually.
introduced additional security measures to prevent supply-chain attacks on npm, following a series of high-impact attacks on the platform.However, the measures are being implemented gradually.
The 2026 CISO Budget Benchmark
It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.