Ransomware payments hit record low: only 23% Pay in Q3 2025
Only 23% of ransomware victims paid in Q3 2025, the lowest ever, continuing a six-year decline in payment rates, Coveware reports.
Cybersecurity firm Coveware reports that only 23% of ransomware victims paid attackers in Q3 2025, the lowest rate ever recorded. The researchers note this continues a six-year decline in payment rates. After 28% of victims paid in early 2024, rates briefly rose before dropping again, showing that fewer breached companies are paying the ransom.
The average ransom payment dropped to $376,941 in Q3 2025 (down 66% from Q2), while the median fell to $140,000 (down 65%). Large firms are refusing to pay, realizing ransoms rarely stop data leaks. Meanwhile, groups like Akira and Qilin target mid-sized firms with smaller, more frequent demands, using a high-volume, low-demand model that’s proving more effective against less resilient victims.
“Ransom payment rates across all impact scenarios — encryption, data exfiltration, and other extortion — fell to a historical low of 23% in Q3 2025.” reads the report. “This continuation of the long-term downward trend is something all industry participants should take a moment to reflect on: that cyber extortion’s overall success rate is contracting.”
Experts see the drop in ransom payments as evidence of progress. Each avoided payment cuts off attackers’ Bitcoin “oxygen.” Experts believe that continued joint effort from defenders, law enforcement, and industry can further shrink the cyber extortion economy to zero, although it’s my personal opinion that the growing automation of attacks and the level of sophistication achieved through the use of AI will make it difficult to completely eliminate criminal activity.
Coveware observed that ransom payments in data exfiltration-only attacks dropped to a record low of 19% in Q3 2025, despite a surge in such incidents. The decline reflects growing maturity among enterprises and cyber response teams, especially privacy attorneys. Paying to suppress data leaks is now widely discouraged, as even “nuisance payments” sustain the extortion economy and conflict with best practices.
Mid-sized companies tend to pay smaller ransoms after attacks because they can’t afford large sums and are easier to disrupt. Ransomware groups like Akira and Qilin exploit this with a high-volume, low-demand strategy.
“Smaller organizations cannot afford large ransoms but remain easier to disrupt. Groups like Akira and Qilin are increasingly leveraging this high-volume, low-demand strategy,”continues the report.
In Q3, attackers kept using the same main entry points, remote access compromise, phishing, and software vulnerabilities. Remote access made up over half of incidents, driven by weak credentials and poor configuration hygiene. Social engineering often merged with technical access, as attackers tricked staff into granting entry. Exploited software flaws were mostly old, unpatched bugs, showing that poor procedures still enable breaches.
In Q3, ransomware groups stayed opportunistic, exploiting easy entry points like unpatched systems, exposed remote access, and stolen credentials. They targeted scale and weak configurations over specific industries. If ransomware-as-a-service actors shift to more targeted attacks, future data will reveal that trend.
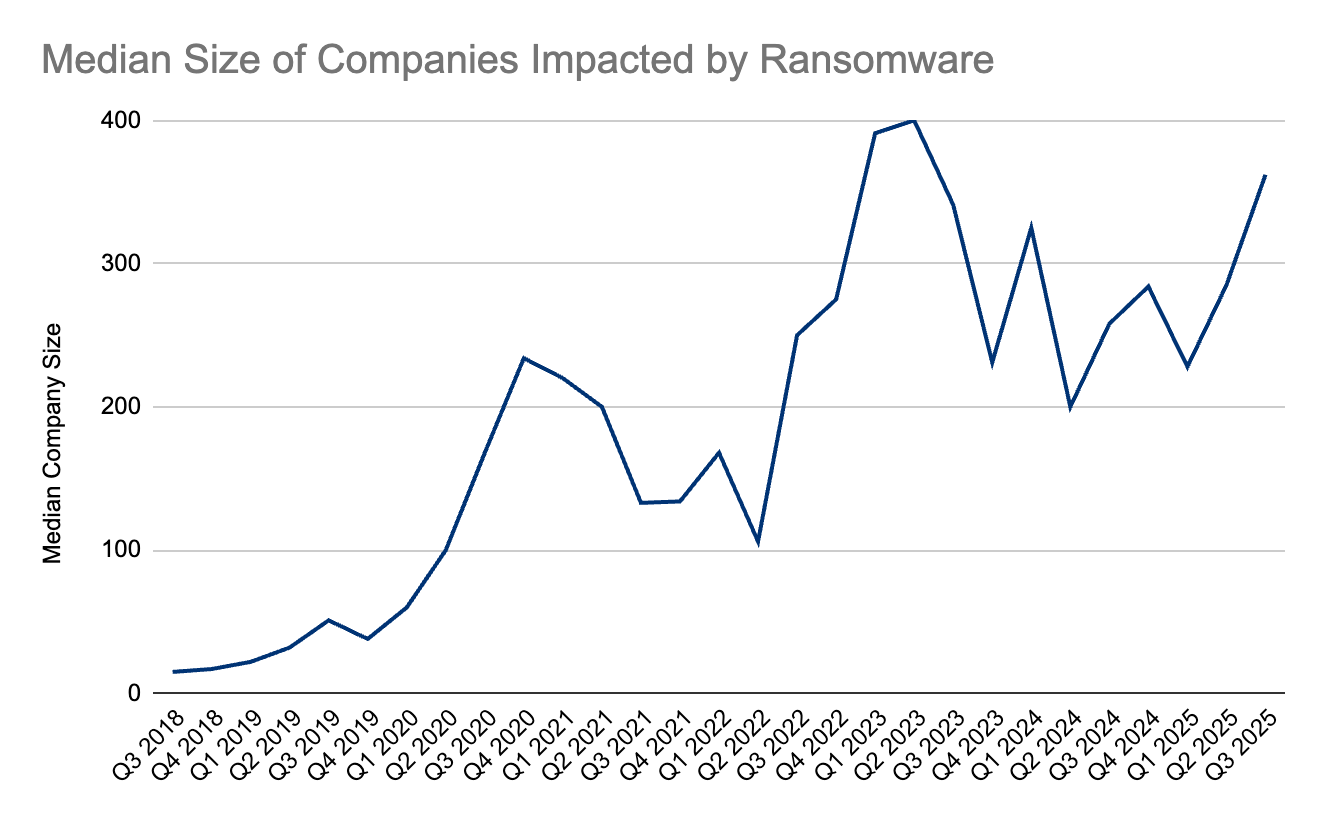
“The median company size of enterprises impacted by a cyber extortion incident was 362 employees (up 27% from Q2 2025) in Q3 2025. The fact that payment frequency and payment amounts are down — a notable paradox that challenges the “big game hunting” assumption that larger targets guarantee bigger payouts.” concludes the report. “This suggests that while attackers may invest more to reach larger organizations, the return on investment is not assured.”
Follow me on Twitter:@securityaffairsandFacebookandMastodon
(SecurityAffairs–hacking,ransomware)