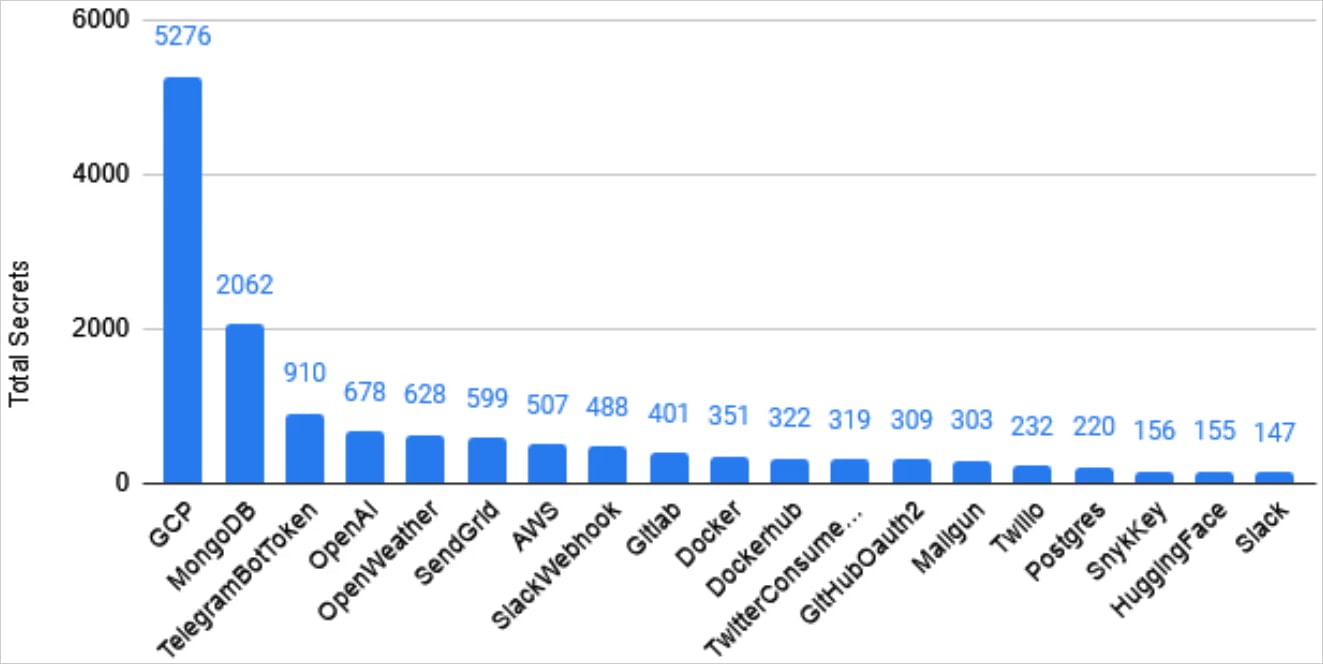
After scanning all 5.6 million public repositories on GitLab Cloud, a security engineer discovered more than 17,000 exposed secrets across over 2,800unique domains.
Luke Marshallused the TruffleHogopen-source tool to check the code in the repositories forsensitive credentials like API keys, passwords, and tokens.
The researcherpreviously scanned Bitbucket, where he found 6,212 secretsspread over 2.6 million repositories. He also checked the Common Crawl datasetthat is used to train AI models, which exposed 12,000 valid secrets.
 describes Marshall.
describes Marshall.
“This setup allowed me to complete the scan of 5,600,000 repositories in just over 24 hours.”
The total cost for the entire public GitLab Cloud repositories using the above method was $770.
The researcher found 17,430 verified live secrets, nearly three times as many as in Bitbucket, and with a 35% higher secret density (secrets per repository), too.
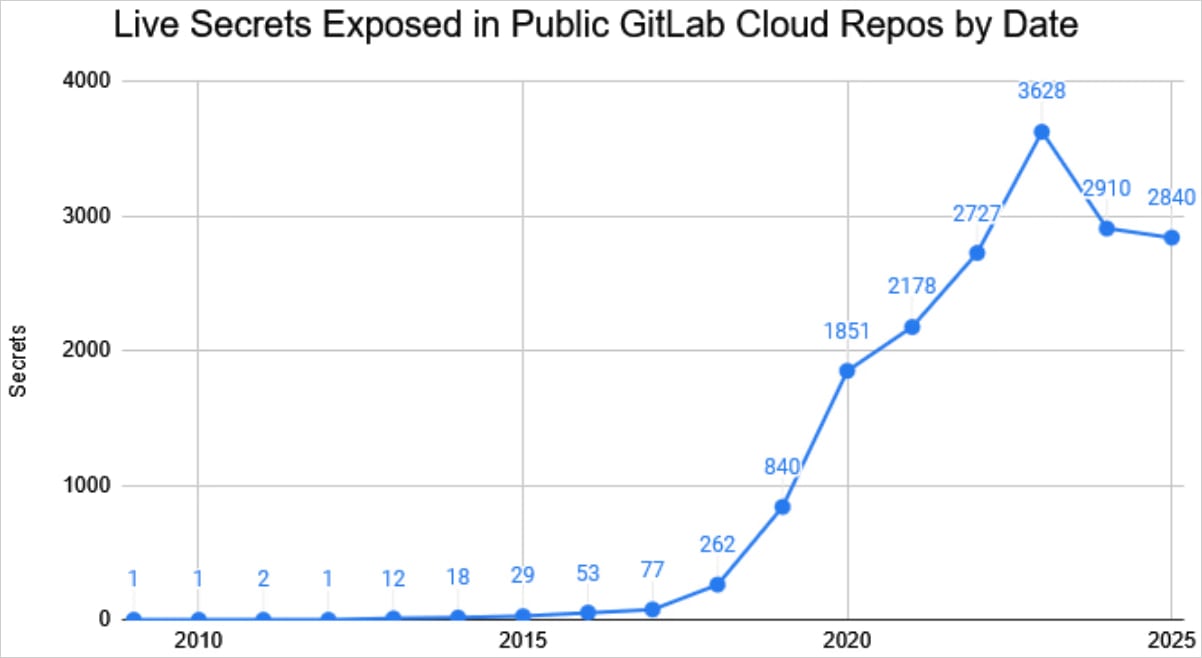
Historical data shows that most leaked secrets are newer than 2018. However, Marshall also found some very older secrets dating from 2009, which are still valid today.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
Bill Toulas
Bill Toulas is a tech writer and infosec news reporter with over a decade of experience working on various online publications, covering open-source, Linux, malware, data breach incidents, and hacks.