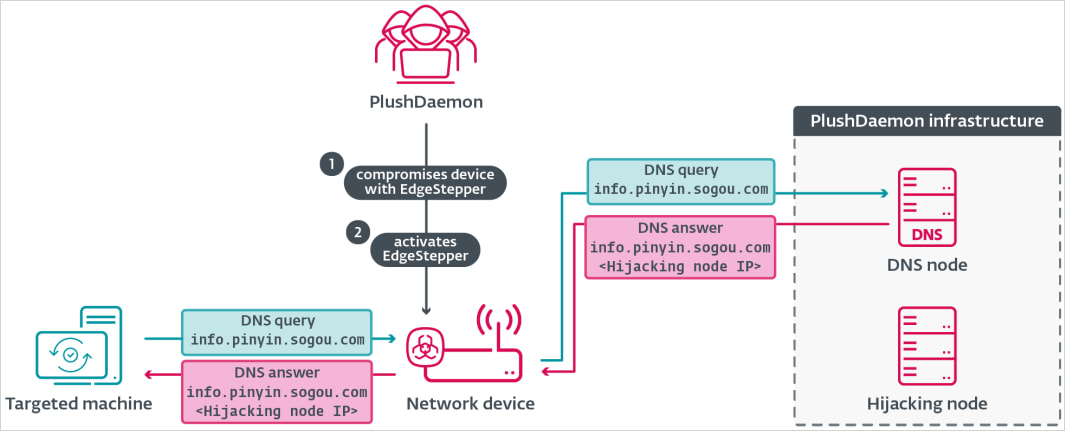
A China-linked threat actor tracked as ‘PlushDaemon’is hijacking software update traffic using a new implant called EdgeStepper in cyberespionage operations.
Since 2018, PlushDaemon hackers have targeted individuals and organizations in the United States, China, Taiwan, Hong Kong, South Korea, and New Zealand with custom malware, such as the SlowStepper backdoor.
PlushDaemon has compromisedelectronics manufacturers, universities, and a Japanese automotive manufacturing plant in Cambodia. Telemetry data from cybersecurity firm ESET indicates that since 2019, the threat actor has relied on malicious updates to breach target networks.

.jpg) report shared with BleepingComputer.
report shared with BleepingComputer.
When a victim tries to update their software, they receive the first-stage malware downloader for Windows called LittleDaemon, which is disguised as a DLL file named ‘popup_4.2.0.2246.dll.’
 previously documented in attacks against users of the South Korean VPN product IPany. During those attacks,users downloaded a trojanized installer from the vendor’s official website.
previously documented in attacks against users of the South Korean VPN product IPany. During those attacks,users downloaded a trojanized installer from the vendor’s official website.
The SlowStepper malware enableshackers to collectdetailed system information, execute extensive file operations, run commands, and use various Python-based spyware tools that can steal data from the browser, intercept keystrokes, and collect credentials.
ESET researchers said that they examined PlushDaemon’s hijacking of Sogou Pinyin, a software input method that is very popular in China, but they observed other product updates being hijacked in the same way.
Theynote that the PlushDaemon’sadversary-in-the-middle capabilities are strong enough “to compromise targets anywhere in the world.”
The report published today includes technical details for all the newly uncovered malware as well as a set of indicators of compromise for files, IP addresses, and domains that PlushDaemon used in attacks that deeployed the EdgeStepper network implant.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
Bill Toulas
Bill Toulas is a tech writer and infosec news reporter with over a decade of experience working on various online publications, covering open-source, Linux, malware, data breach incidents, and hacks.