For the first time, a RomCom payload has been observed being distributed via SocGholish.
RomCom malware used the SocGholish fake update loader to deliver Mythic Agent to a U.S. civil engineering firm.
In September 2025, Arctic Wolf Labs observed RomCom threat actors delivering the Mythic Agent via SocGholish to a U.S. company. The researchers noticed that the payload executed about 10 minutes after initial exploitation, marking the first time RomCom used SocGholish. Arctic Wolf attributes the attack with medium-to-high confidence to Russia’s GRU Unit 29155, which targets entities supporting Ukraine, highlighting RomCom’s focus on victims linked to Ukraine globally.
RomCom, active since mid-2022 and aligned with Russian interests, consistently targets organizations linked to Ukraine, even loosely. The group, also known as Storm-0978 or UNC2596, is believed to be a nation-state actor due to its advanced capabilities. As the Russia-Ukraine war persists, RomCom has expanded its operations, launching opportunistic attacks worldwide, including against U.S.-based pro-Ukrainian entities.
SocGholish, a malware delivery framework active since 2017, has evolved from a nuisance threat into a key initial access vector for major ransomware groups, including those linked to EvilCorp. It spreads through malicious JavaScript injected into compromised websites and uses fake browser-update prompts to trick users into downloading payloads. Once executed, it exfiltrates data, establishes persistence, enables remote access, and installs follow-on malware.
Recent campaigns show large-scale use of compromised legitimate sites and an expanding distribution network operated by TA569. In the case analyzed, SocGholish directly deployed RomCom’s targeted loader, disguised as msedge.dll, with a hardcoded domain to ensure execution only on the intended victim.
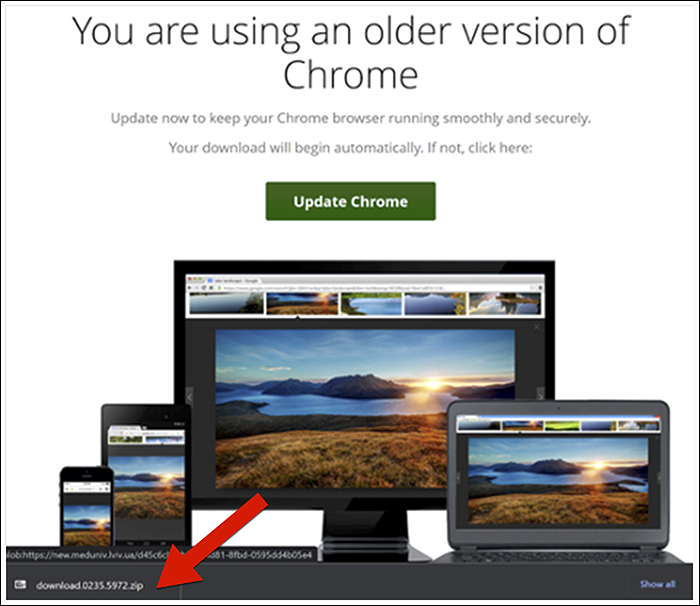
SocGholish spreads by injecting malicious JavaScript into vulnerable legitimate websites, often exploiting outdated plugins or remote-code-execution flaws to display FAKEUPDATE popups that trick users into manually downloading malware disguised as browser updates.
“While SocGholish can also be spread byphishingtactics, including email phishing, the lures themselves deviate from the tried-and-tested norms of phishing campaigns, as they operate without the typical calls to action, sense of urgency, threats, or promises of reward.” reads the report published by Arctic Wolf. “Instead, they weaponize the end-user’s security training, no matter how basic, by displaying a simple fake update popup. When the user manually clicks “Update”, a malware payload is downloaded to their device.”
It also leverages traffic-direction systems to funnel targeted visitors to compromised sites. Once executed, the payload connects to a SocGholish C2 server, enabling reconnaissance, remote commands, and delivery of follow-on malware such as the VIPERTUNNEL backdoor. In the Arctic Wolf case, the infection chain progressed through obfuscated JavaScript, PowerShell-based reconnaissance, and Mythic C2 testing before RomCom’s loader was deployed.
RomCom used a loader called msedge.dll to deploy a Mythic agent only when the victim’s domain matched a hardcoded value. The loader decrypted and executed shellcode that contacted a Mythic C2, but Arctic Wolf’s defenses quarantined it before execution. Investigators linked seven C2 domains, mostly registered on the same day, to RomCom. The U.S. civil-engineering target had prior ties to a Ukraine-linked city, aligning with RomCom’s pro-Russia targeting.
“This is the first time a RomCom payload has been observed being distributed by SocGholish. SocGholish has previously been seen delivering Raspberry Robin, malwareassessedby the FBI, CISA, and NSA to be strongly associated with Russia’s GRU 161st Specialist Training Center, otherwise known asUnit 29155.” concludes the report. “The timeline from infection via FAKEUPDATE to the delivery of RomCom’s loader was less than 30 minutes. Delivery is not made until the target’s Active Directory domain had been verified to match a known value provided by the threat actor.”
Follow me on Twitter:@securityaffairsandFacebookandMastodon
(SecurityAffairs–hacking,RomCom)