2 minutes ago
Alert, Cyber Attack, National
Mysterious Elephant is an active APT group identified by Kaspersky GReAT in 2023. It continually evolves its tactics to avoid detection.
The group’s recent campaign, starting in early 2025, shows a notable change in their tactics, focusing more on new custom tools and open-source tools like BabShell and MemLoader.
The group’s new campaign from early 2025 shows a big change in their tactics. They now use exploit kits, phishing emails, and malicious documents to access targets. Once inside, they utilize both custom and open-source tools.
Mysterious Elephant runs a sophisticated network of domains and IP addresses, employing wildcard DNS records to generate unique domain names for each request, complicating tracking for security researchers. They host their operations on virtual private servers (VPS) and cloud services, which helps them remain undetected. Our data reveals that this APT group utilizes multiple VPS providers, but they seem to favor certain ones.
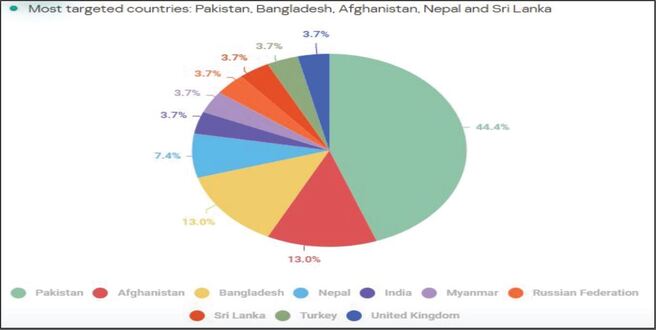
Mysterious Elephant mainly targets governments and foreign affairs in the Asia-Pacific. They focus on Pakistan, Bangladesh, and Sri Lanka, with fewer attacks in other countries. The group employs custom payloads aimed at specific individuals, showcasing their sophistication in targeted attacks.
The group’s victim targeting is very focused. Attackers typically use personalized phishing emails and harmful documents to gain access. After entering, they use various tools to elevate their permissions, navigate through the network, and steal sensitive data.
Organizations must adopt strong security measures to combat the Mysterious Elephant threat, such as regular software updates, network monitoring, and employee training. International cooperation and sharing information among cybersecurity experts, governments, and industries are also vital for tracking and disrupting this group’s activities.