New Mirai variant ShadowV2 tests IoT exploits amid AWS disruption
ShadowV2, a new Mirai-based botnet, briefly targeted vulnerable IoT devices during October’s AWS outage, likely as a test run.
During the late-October AWS disruption, FortiGuard Labs researchers observed the Mirai-based ‘ShadowV2’ malware exploiting IoT vulnerabilities across multiple countries and industries. The botnet was active only during the outage, suggesting a test run for future attacks. ShadowV2 targets IoT devices using flaws in products from DDWRT (CVE-2009-2765), D-Link(CVE-2020-25506, CVE-2022-37055, CVE-2024-10914, CVE-2024-10915), DigiEver (CVE-2023-52163), TBK(CVE-2024-3721), TP-Link(CVE-2024-53375).
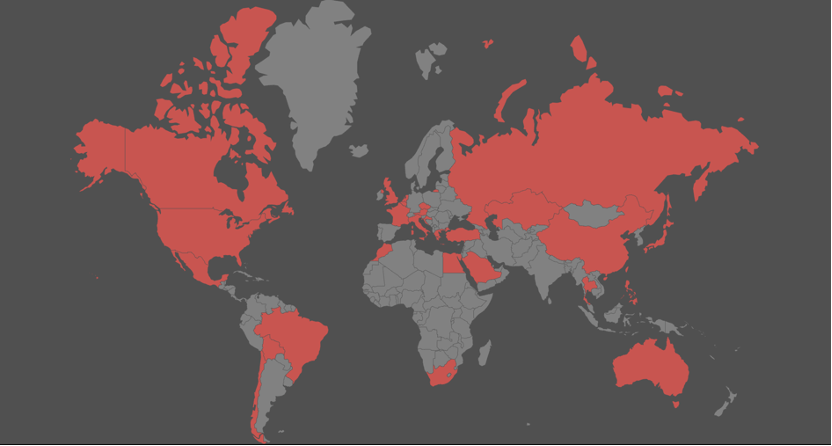
The bot targeted devices in multiple countries worldwide, including:
- Oceania: Australia
- America: Canada, United States, Mexico, Brazil, Bolivia, Chile
- Europe: United Kingdom, Netherlands, Belgium, France, Czechia, Austria, Italy, Croatia, Greece
- Africa: Morocco, Egypt, South Africa
- Asia: Turkey, Saudi Arabia, Russia, Kazakhstan, China, Thailand, Japan, Taiwan, Philippines
Fortinet reported victims in multiple industries, including technology, retail and hospitality, manufacturing, managed security services providers, government, telecommunication and carrier services, and education.
ShadowV2 spreads through multiple IoT vulnerabilities, dropping the downloader script binary.sh from 81[.]88[.]18[.]108.
The malware resembles the Mirai LZRD variant, decoding its configuration with XOR key 0x22 and loading paths, headers, and User-Agent strings. After resolving its C2 domain, it connects to 81[.]88[.]18[.]108 and identifies itself as ShadowV2 Build v1.0.0 for IoT. It then initializes a wide range of UDP, TCP, and HTTP flood methods, waits for C2 commands, and launches DDoS attacks based on received parameters.
“ShadowV2 supports two transport-layer protocols (UDP and TCP) and the HTTP application protocol. Implemented attack methods including UDP floods, several TCP-based floods, and HTTP-level floods. The malware maps these behaviors to internal function names, such asUDP, UDP Plain, UDP Generic, UDP Custom, TCP, TCP SYN, TCP Generic, TCP ACK, TCP ACK STOMP,andHTTP.” reads the report published by Fortinet. “It listens for commands from its C2 server and triggers DDoS attacks using the corresponding attack method ID and parameters.”
ShadowV2 shows that IoT devices are still a major security weak point. Its evolution signals that threat actors are increasingly focusing on IoT environments.
“The evolution of ShadowV2 suggests a strategic shift in the targeting behavior of threat actors toward IoT environments.” concludes the report. “This underscores the importance of maintaining timely firmware updates, enforcing robust security practices, and continuously monitoring relevant threat intelligence to strengthen overall situational awareness and ensure ecosystem resilience.”
Follow me on Twitter:@securityaffairsandFacebookandMastodon
(SecurityAffairs–hacking,ShadowV2 botnet)