Attackers deliver ShadowPad via newly patched WSUS RCE bug
Attackers exploited a patched WSUS flaw (CVE-2025-59287) to gain access, use PowerCat for a shell, and deploy the ShadowPad malware.
AhnLab SEcurity intelligence Center (ASEC) researchers reported that threat actors exploited a recently patched WSUS flaw (CVE-2025-59287) to deliver the ShadowPad malware.
ShadowPad is a backdoor widely used by China-linked APT groups and privately sold to them. After gaining access to WSUS-enabled servers, the attackers used PowerCat to obtain a system shell, then downloaded and installed ShadowPad via certutil and curl. The researchers detailed the intrusion chain, ShadowPad’s operation, and recommended defenses.
In October, Microsoftreleasedan out-of-band fix forCVE-2025-59287 (CVSS score of 9.8) that is under active exploitation. Researchers MEOW and Markus Wulftange of CODE WHITE GmbH reported the vulnerability.
The flawis a deserialization of untrusted data in Windows Server Update Service that allows an unauthorized attacker to execute code over a network. Remote, unauthenticated attackers can trigger unsafe deserialization of AuthorizationCookie objects in the GetCookie() endpoint, leading to RCE with SYSTEM privileges. The issue stems from insecure BinaryFormatter use, which Microsoft deprecated and removed from .NET 9 in 2024 due to inherent security risks.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA)addedthe flaw to its Known Exploited Vulnerabilities catalog, while Hawktrace researcherspublished a PoCfor this vulnerability.
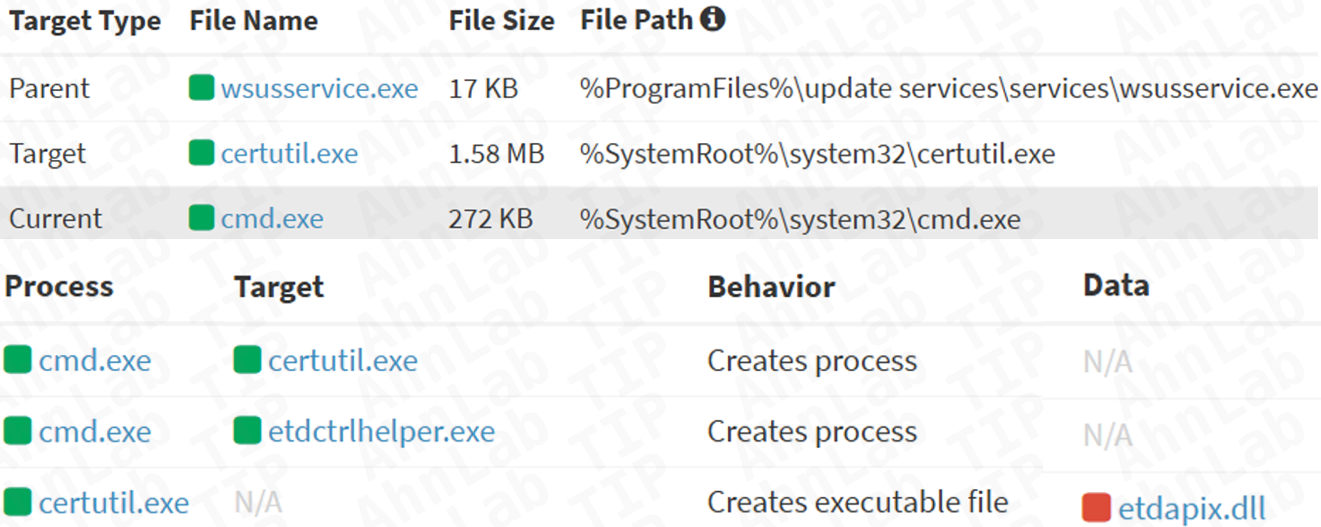
According to ASEC, attackers exploited the WSUS RCE flaw CVE-2025-59287 to break into Windows Server systems with WSUS enabled. After the PoC dropped, they ran PowerCat to open a remote CMD shell. On November 6th, they used the same flaw again to run curl and certutil, pulled ShadowPad components from a remote server, decoded them, and installed the malware directly onto the system.
“After gaining initial access, the threat actor exploited the same vulnerability on November 6th to execute curl.exe and certutil.exe, which are legitimate Windows utilities, to install the ShadowPad malware.” reads the report.
ShadowPad uses DLL sideloading, not a standalone EXE. In the attack detailed by ASEC, ETDCtrlHelper.exe loads a malicious DLL (ETDApix.dll) that runs the ShadowPad loader in memory, while a .tmp file holds its core backdoor logic. The malware persists under the name Q‑X64, sets scheduled tasks, uses several startup paths, and injects into system processes. It contacts its C2 at 163.61.102[.]245 via HTTP/HTTPS using spoofed Firefox headers.
“After the proof-of-concept (PoC) exploit code for the vulnerability was publicly released, attackers quickly weaponized it to distribute ShadowPad malware via WSUS servers. This vulnerability is critical because it allows remote code execution with system-level permission, significantly increasing the potential impact.” concludes the report.
Organizations using WSUS should patch CVE‑2025‑59287, restrict WSUS access to Microsoft Update servers, block unwanted traffic on ports 8530/8531, and audit for suspicious activity such as PowerShell, certutil, curl usage and abnormal network connections.
Follow me on Twitter:@securityaffairsandFacebookandMastodon
(SecurityAffairs–hacking, CVE‑2025‑59287)