Academic researchers developed a side-channel attack called TEE.Fail, which allows extracting secrets from the trusted execution environmentin the CPU, the highly secure area of a system, such asIntel’sSGX and TDX, and AMD’s SEV-SNP.
The method is amemory-bus interposition attack on DDR5 systems that could be successfully done by computer hobbyists a cost of less than $1,000.
Trusted Execution Environments (TEEs) are “confidential computing” hardware withinthe main processor that ensure confidentiality and integrity of sensitive data, like cryptographic keys used for authentication and authorization.
This environment is isolated from the operating system and creates protectedregions of memory where code and data can run securely.
Researchers from Georgia Tech and Purdue University note thatmodern implementations of Intel SGX, Intel TDX, and AMD SEV-SNP are no longer as secure as advertised, due to architectural trade-offs in recent generations.
Specifically, TEEs moved from client CPUs to server-grade hardware using DDR5 memory, which adopted deterministic AES-XTS memory encryption and stripped away memory integrity and replay protections in favor of performance and scalability.
Their experiments confirmed that it is possible to exploit these weaknesses for key extraction and attestation forgery. TEE.Failis the first DDR5-based ciphertext attack, extending prior DDR4 work like WireTap and BatteringRAM.
Attack and implications
The attack requires physical access to the target as well as root-level privileges for Kernel driver modification, but no chip-level expertise.
In the technical paper, the researchers explain that they were able to capture the signal reliably by reducingthesystem’s memory clock to 3200 MT/s (1.6 GHz). For this, they attached aRDIMM riser and a custom probe isolation network between a DDR5 DIMM and the motherboard.

 sysfs.”
sysfs.”
This let them find the info for determining the DIMM location for the physical address.
However,SGX uses the OS kernel for physical memory allocation and the researchers had to “modify thekernel’s SGX driver to accept a virtual and physical addresspair as a parameter to be stored in global kernel memory.”
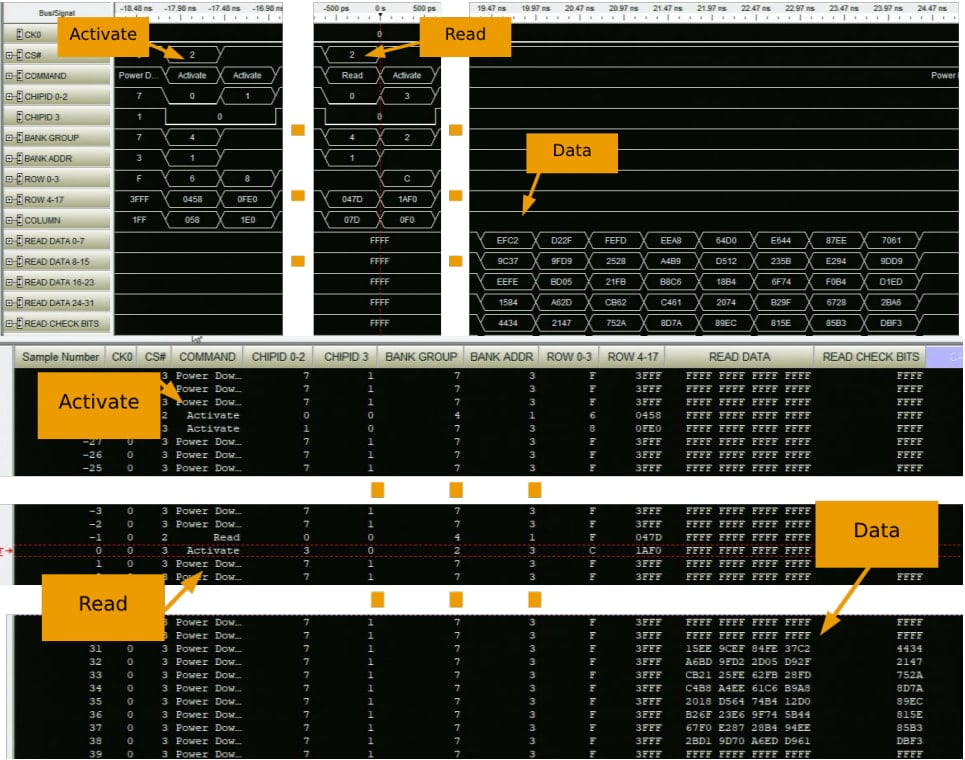
The researchers say that they created an SGX enclave that bombardeda specific memory virtual address with read and write operations. This let them verify that the encrypted ciphertext observed on the memory interposer was a deterministic function of the physical memory address and its contents.
“To check that encryption is deterministic, weinstruct our enclave to perform a series of write and readoperations to a fixed virtual address in enclave memory,capturing the ciphertext read data after each step usingour logic analyzer,” they explain.
Because of the use of the AES-XTSencryption, where a piece of information is encrypted to the same output every time,the team wrote known values to the observable physical addresses to build a ciphertext to value mapping.
Bill Toulas
Bill Toulas is a tech writer and infosec news reporter with over a decade of experience working on various online publications, covering open-source, Linux, malware, data breach incidents, and hacks.