The Pwn2Own Ireland2025 hacking competition has ended with security researchers collecting $1,024,750 in cash awardsafter exploiting 73 zero-day vulnerabilities.
At Pwn2Own Ireland 2025, competitors targeted products in eight categories, includingprinters, network storage systems, messaging apps, smart home devices, surveillance equipment, home networking equipment, flagship smartphones (Apple iPhone 16, Samsung Galaxy S25,and Google Pixel 9), and wearable technology (including Meta’s Ray-Ban Smart Glasses and Quest 3/3S headsets).
This year’s contest also expandedthe attack surface to include USB port exploitation on mobile handsets, requiring researchersto hack locked devices via a physical connection. However, traditional wireless protocols like Bluetooth, Wi-Fi, and NFC (near-field communication) remainedvalid attack vectors.
Thehacking contest, co-sponsored byMetaalongside QNAP and Synology, tookplace from October 21 to October 23 in Cork, Ireland.
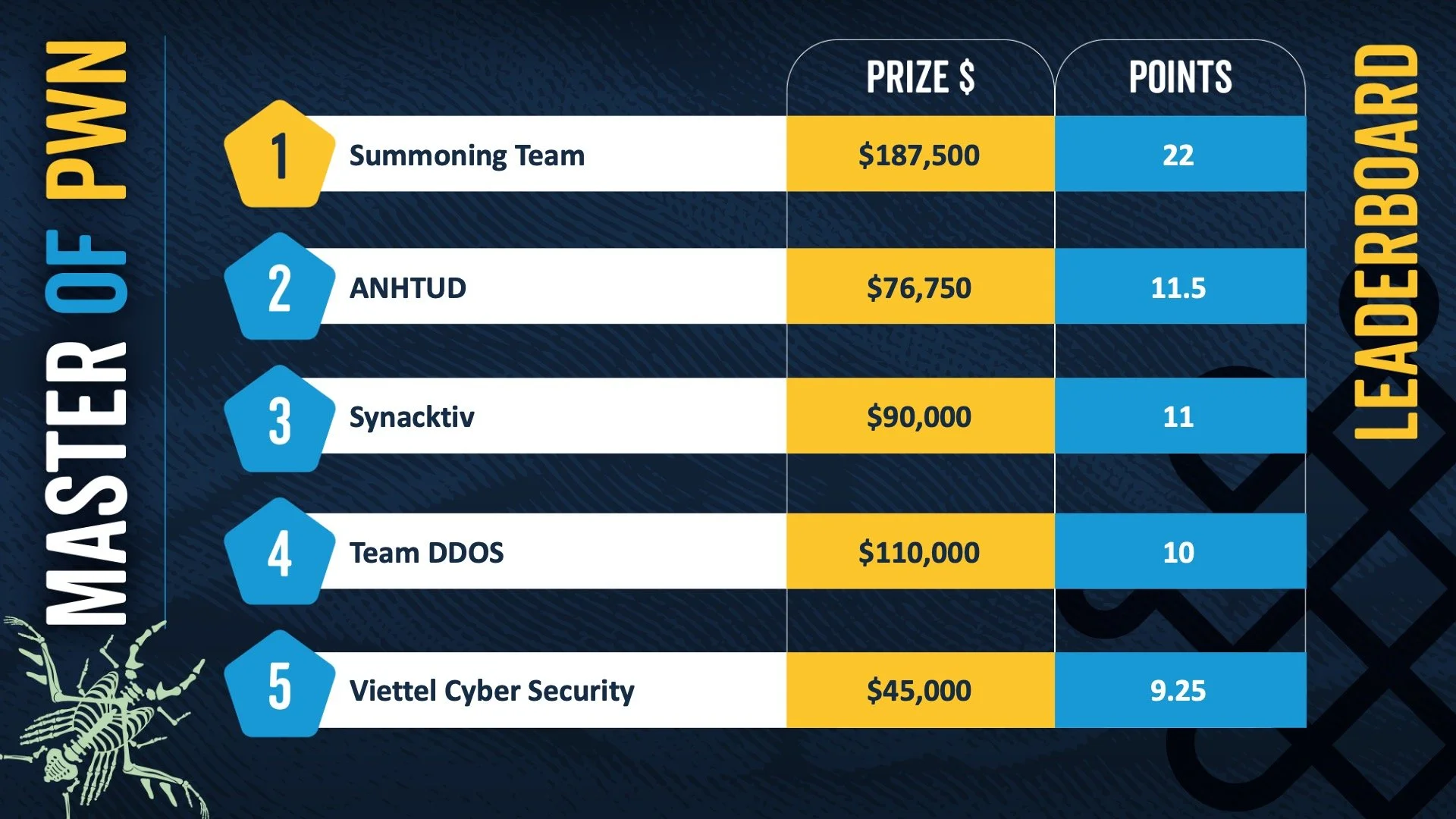
Summoning Team won this year’s edition of Pwn2Own Ireland with22 Master of Pwn points and $187,500 earned throughout the three-day event after hacking the Samsung Galaxy S25, the Synology DiskStation DS925+ NAS,the Home Assistant Green, the Synology ActiveProtect Appliance DP320 NAS drive, the Synology CC400W camera, and the QNAP TS-453E NAS device.
Team ANHTUD secured the second position with $76,750 and 11.5 Master of Pwn points, while Team Synactiv took third place with $90,000 in prizes and 11 Master of Pwn points.
 exploited 34 unique zero-days and collected 2,500 in cash awards. On the second day of the event, they demoed another 22 unique zero-day vulnerabilities for $267.500.
exploited 34 unique zero-days and collected 2,500 in cash awards. On the second day of the event, they demoed another 22 unique zero-day vulnerabilities for $267.500.
The highlight of the last day was the Samsung Galaxy S25 gettinghacked by Interrupt Labs’ team via an improper input validation bug, who earned 5 Master of Pwn points and $50,000 after also enabling location tracking andthe camera in the process.
WhileTeam Z3 was also scheduled today todemonstrate a WhatsApp Zero-Click remote code execution zero-day, eligible fora $1 million reward, they withdrew from the competition. They chose to disclose their findings privately to ZDI analysts before sharing their research with Meta’s engineering team.
The Zero Day Initiative (ZDI) organizes this hackingcontestto identify security vulnerabilities before threat actors can exploit them in attacks andcoordinate responsible disclosure with the affected vendors.
After the zero-daysare exploited at Pwn2Own, the vendors have 90 days to release patches before Trend Micro’s Zero Day Initiative publicly discloses them.
In January 2026, the ZDI will once again be atthe Automotive World technology show in Tokyo, Japan,for the third Pwn2Own Automotive contest, again sponsored by Tesla
