PhantomCaptcha targets Ukraine relief groups with WebSocket RAT in October 2025
PhantomCaptcha phishing campaign hit Ukraine relief groups with a WebSocket RAT on Oct 8, 2025, targeting Red Cross, UNICEF, and others.
SentinelOne researchers uncovered PhantomCaptcha, a coordinated spear-phishing campaign on October 8, 2025, targeting Ukraine war relief groups, including Red Cross, UNICEF, NRC, and local administrations. Threat actors used fake emails to deploy a WebSocket-based remote access trojan for command-and-control.
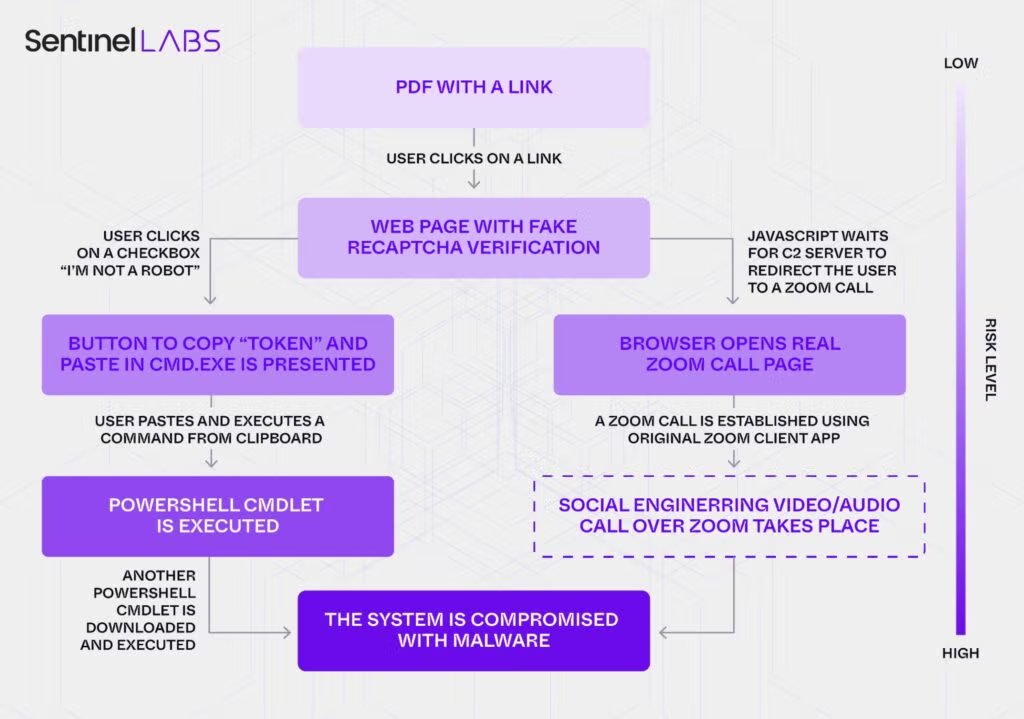
The attackers used emails impersonating the Ukrainian President’s Office with weaponized PDF documents, luring victims into executing malware via a ‘ClickFix’-style fake Cloudflare captcha page.
The documents include an embedded link that redirects victims to a fake Zoom site (“zoomconference[.]app”) and tricks them into running a malicious PowerShell command.
“The PhantomCaptcha campaign employed a sophisticated multi-stage attack chain designed to exploit user trust and bypass traditional security controls.” reads the report published by SentinelOne.
“Opening the weaponized PDF and clicking on the embedded link directed the victim tozoomconference[.]app, a domain masquerading as a legitimate Zoom site but in reality hosting a VPS server located in Finland and owned by Russian provider KVMKA.”
The PhantomCaptcha campaign delivered a three-stage PowerShell payload. Stage 1 used a huge, obfuscated downloader script (cptch) that simply fetched a second-stage “maintenance” payload. Stage 2 fingerprinted the host (name, domain, user, UUID, PID), sent XOR-encrypted data to a C2 URL, disabled PowerShell history, then received an encrypted stage-3 payload. Stage 3 ran an in-memory WebSocket RAT that accepts Base64/JSON commands (sync cmd or async psh) and executes them. Then Stage 3 returns output and system identifiers, and keeps persistent reconnect logic, effectively providing the operator with a remote shell.
“The final payload is a WebSocket RAT hosted on Russian-owned infrastructure that enables arbitrary remote command execution, data exfiltration, and potential deployment of additional malware,” continues the report. “The WebSocket-based RAT is a remote command execution backdoor, effectively a remote shell that gives an operator arbitrary access to the host.”
The researchers noted that PhantomCaptcha demonstrated moderate OPSEC, remaining active for approximately 24 hours on October 8, 2025. Its C2 domain, zoomconference[.]app, was hosted on a Russian KVMKA VPS (193.233.23[.]81). Investigators later linked related IPs (45.15.156[.]24 (goodhillsenterprise[.]com) and 185.142.33[.]131 (bsnowcommunications[.]com))to the same threat actors. While the lure infrastructure went offline quickly, the backend C2 remained active, suggesting compartmentalization. SentinelOne reported that attackers registered a new domain, zoomconference[.]click, the next day, hints at ongoing operations.
Researchers found that the weaponized 8-page PDF tied to PhantomCaptcha was uploaded from Ukraine, India, Italy, and Slovakia, showing broad targeting. SentinelOne traced the campaign’s setup to March 27, 2025, when attackers registered goodhillsenterprise[.]com to host obfuscated PowerShell malware. The zoomconference[.]app domain was active only for one day on October 8. Investigators also uncovered fake Android apps on princess-mens[.]click, designed to steal data like contacts, media, and location. While attribution remains unclear, the use of ClickFix suggests a possible link to the campaign to the Russian APT group COLDRIVER.
“The PhantomCaptcha campaign reflects a highly capable adversary, demonstrating extensive operational planning, compartmentalized infrastructure, and deliberate exposure control.” concludes the report. “The six-month period between initial infrastructure registration and attack execution, followed by the swift takedown of user-facing domains while maintaining backend command-and-control, underscores an operator well-versed in both offensive tradecraft and defensive detection evasion.”
Follow me on Twitter:@securityaffairsandFacebookandMastodon
(SecurityAffairs–hacking,Ukraine)