State-sponsored Iranian hacker group MuddyWater has targeted more than 100 government entities in attacks that deployed version 4 of the Phoenix backdoor.
The threat actor is also known as Static Kitten, Mercury, andSeedworm, and ittypically targets government and private organizations in the Middle East region.
Starting August 19, the hackers launched a phishing campaign from a compromised account that they accessed through the NordVPN service.
The emails were sent to numerousgovernment and international organizations in the Middle East and North Africa, cybersecurity companyGroup-IB says in a report today.
According to the researchers, the threat actor took down the server and server-side command-and-control (C2) component on August 24, likely indicating a new stage of the attack that relied on other tools and malware to gather information from compromised systems.
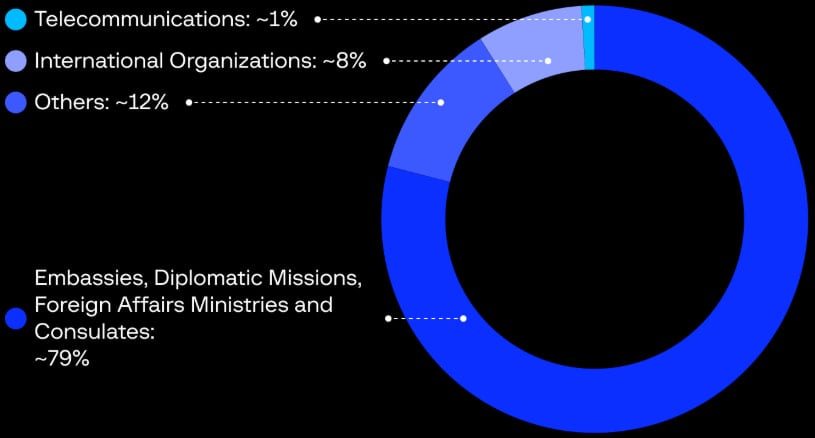
Most of the targets of this MuddyWater campaign are embassies, diplomatic missions, foreign affairs ministries, and consulates.
 research revealed that MuddyWater used emails with malicious Word documents with macro code that decoded and wrote to disk the FakeUpdate malware loader.
research revealed that MuddyWater used emails with malicious Word documents with macro code that decoded and wrote to disk the FakeUpdate malware loader.
The emails attach malicious Word documents that instruct recipients to “enable content” on Microsoft Office. This action triggers a VBA macro that writes the ‘FakeUpdate’ malware loader on the disk.
It is unclear what prompted MuddyWater to deliver malware through macro code hidden in Office documents, since the technique was popular several years ago, when macros ran automatically upon opening a document.
Since Microsoft disabled macros by default, threat actors moved to other methods, a more recent one being ClickFix, also used by MuddyWater in past campaigns.
Group-IB researchers say that the loader in MuddyWater’s more recent attacks decrypts the Phoenix backdoor, which is an embedded, AES-encryptedpayload.
The malware is written to‘C:ProgramDatasysprocupdate.exe,’ and establishes persistence by modifying the Windows Registry entry with configurations for the current user, including the app that should run as theshell after logging into the system.
Bill Toulas
Bill Toulas is a tech writer and infosec news reporter with over a decade of experience working on various online publications, covering open-source, Linux, malware, data breach incidents, and hacks.
