Article written by Andrius Buinovskis, head of product at NordLayer
Even though gateways are integral to a network security strategy, they are often not utilized fully from a threat mitigation perspective. Businesses relying on basic gateway configuration are missing out on the opportunity to maximize security, improve workflows, and enhance productivity — all of which could be achieved with the help of a comprehensive gateway security strategy.
There’s no denying that navigating the different approaches to gateway security and identifying the most effective measures can be challenging. In this article, I will explore the key steps to fully optimizing gateways for enhanced security and productivity.
1. Utilizing gateways for network segmentation
Gateways can be configured for network segmentation by creating isolated virtual networks to separate users, teams, or departments based on their roles or functions.
Network segmentation is especially crucial in medium-sized and large corporations due to the expanded attack surface resulting from many users and devices, or small organizations that operate with highly sensitive data.
Gateway-based network segmentation provides centralized control and security between specific parts of the network, acting as the main line of defense between their boundaries and safeguarding access to sensitive information.

Gateway access control policies determine who can access specific resources or network segments. These policies can restrict access based on a user’s role, device type, or location, ensuring that only authorized individuals can reach sensitive resources.
Managing access through gateways and enforcing these tailored policies allows for strict traffic control between networks, adhering to the zero trust principles.
2. Deploying multiple gateways for higher efficiency
Having a single gateway is a high-risk strategy — not only for security, but also for performance. Reliance on a single endpoint leaves the organization at a higher risk of experiencing a slowdown in operations due to outages or exposing the entire network to threats if one user is compromised.
Additionally, relying on a single gateway can create a bottleneck due to the volume of ingoing and outgoing traffic — as the scope increases, the gateway can become overwhelmed, leading to delays and slower performance.
This is especially relevant for bigger teams — bottlenecks are inevitable if hundreds of simultaneous users exist.
To enhance workloads, businesses should implement a distributed gateway architecture. It enables traffic distribution across multiple gateways and eliminates risks caused by a single point of failure. If one of the gateways fails, another can take over.
Additionally, balancing the load helps evenly distribute the traffic across all gateways, preventing bottlenecks. As a result, business operations can run smoothly and without interruptions.
Secure your network and stay compliant with NordLayer
Navigating the complexity of cybersecurity solutions can be overwhelming. As your workforce grows and security requirements evolve, an adaptable and scalable approach is crucial to ensuring seamless protection.
ZTNA-based solutions, a cutting-edge business VPN, Threat Protection, Threat Intelligence, and Password Manager — NordLayer combines all enterprise cybersecurity essentials in one toggle-ready platform, designed to adapt to hybrid infrastructures and integrate seamlessly with existing cybersecurity solutions.
3. Optimize gateways for a distributed workforce
Enforcing cybersecurity can prove challenging as organizations adopt remote or hybrid work models. It’s especially demanding if some employees work from different countries, each with connectivity challenges.
Gateway optimization must account for different locations. Otherwise, the organization can be subject to latency.
If the centralized gateway is located far away from the working area, the data will need to travel longer distances, resulting in users experiencing delays and ultimately affecting performance. Consequently, users might avoid using the gateway and rely on an insecure connection instead.
To prevent this, businesses should deploy geographically distributed private gateways closer to their workforce.
Local privacy laws, such as the GDPR or CCPA, must also be considered when optimizing gateways to ensure traffic routing adheres to jurisdictional restrictions. Otherwise, the organization might risk violating regulatory requirements.
4. Setting up cloud firewalls for an additional layer of protection
Even with proper network segmentation at the gateway level, additional measures are needed to fully mitigate data security risks. Hackers can use various techniques to extract data, such as exploiting open ports and allowed protocols that are not adequately controlled.
Under these conditions, a cloud firewall becomes necessary — it adds a security dimension, acting as the gatekeeper for secure traffic.
A cloud firewall monitors all traffic entering and leaving cloud and on-premise environments, allowing only approved communication channels.
It blocks ports and protocols that could be exploited for malicious purposes, ensuring that only necessary and secure ones are available. For example, suppose users access data primarily through the browser.
In that case, access should be limited to the HTTPS protocol and port 443, while other access methods, including APIs or file transfers, should only be enabled for select users or systems.
Additionally, the firewall should only allow the minimum required ports and protocols for those tasks — this approach helps to reduce the attack surface and prevent data extraction or lateral movement within the network.
Maximizing gateway security with NordLayer
To stay protected in the current cyberthreat landscape, businesses must go beyond basic gateway configuration. A more comprehensive and updated approach to gateway security should include network segmentation, a distributed gateway architecture, optimization for the distributed workforce, and enforced protections, such as granular network segmentation with a cloud firewall to control access at the protocol and port level.
NordLayer offers customizable solutions designed to mitigate potential damage caused by unexpected incidents through proper network segmentation.
NordLayer’s private gateways allow granular access controls for segmented networks, regional gateway deployments for optimized traffic routing, and integrated firewall policies to block specific traffic while adhering to Zero Trust principles.
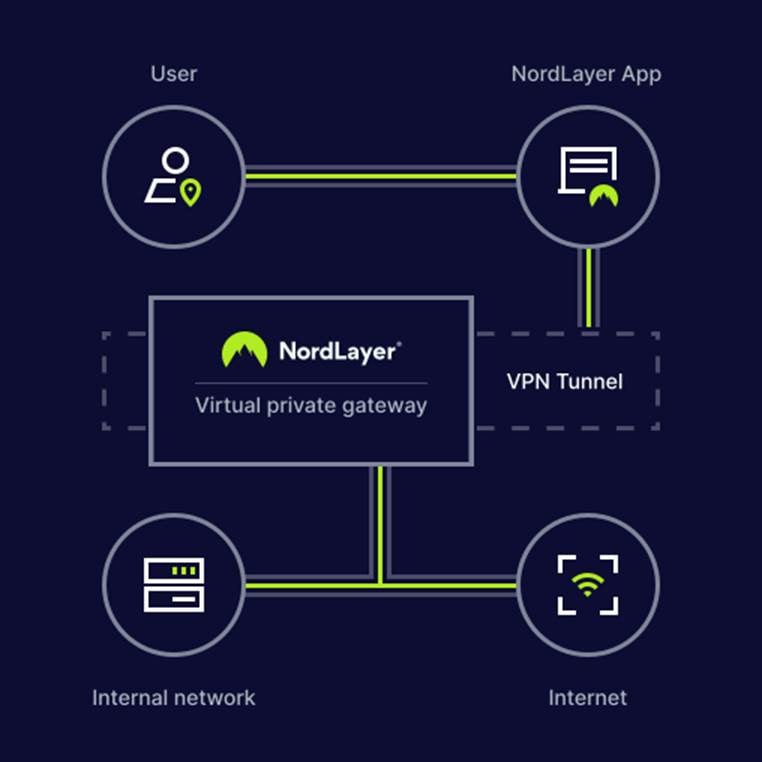
With NordLayer’s comprehensive approach to gateway security, organizations can protect sensitive data, maintain compliance, and ensure uninterrupted performance — no matter where their workforce operates.
To learn more, visit NordLayer.com.
About the author:
Andrius has over 20 years of experience in the IT field and has been keenly interested in cybersecurity since 2015. He now leads his team as the head of product at NordLayer, a toggle-ready network security platform for business.
He drives the development agenda by extensively researching the market, understanding client needs, and assessing technical capabilities. Andrius prioritizes fostering confidence within the product team, empowering it to address intricate security challenges and translate discoveries into enhanced layers of protection for clients.
Sponsored and written by NordLayer.