Uma nova campanha maliciosa tem como alvo os desenvolvedores do macOS com plataformas falsas Homebrew, LogMeIn e TradingView que fornecem malware de roubo de informações como AMOS (Atomic macOS Stealer) e Odyssey.
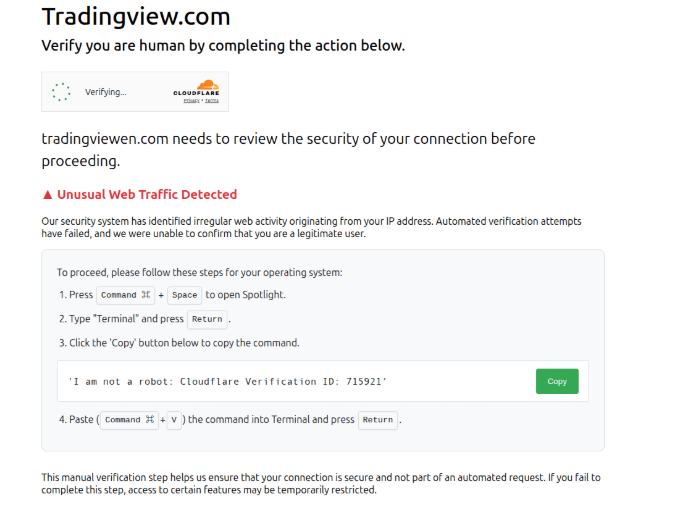
A campanha emprega técnicas “ClickFix” em que os alvos são induzidos a executar comandos no Terminal, infectando-se com malware.
O Homebrew é um popular sistema de gerenciamento de pacotes de código aberto que facilita a instalação de software no macOS e no Linux. Os agentes de ameaças usaram no passado o nome da plataforma para distribuir AMOSem campanhas de malvertising.
O LogMeIn é um serviço de acesso remoto e o TradingView é uma plataforma de gráficos financeiros e análise de mercado, ambos amplamente utilizados pelos usuários da Apple.
Pesquisadores da empresa de caça a ameaças Hunt.io identificaram mais de 85 domínios que se passam pelas três plataformas nesta campanha, incluindo o seguinte:
| http://homebrewclubs.org/ | https://sites-phantom.com/ |
| http://homebrewfaq.org/ | https://tradingviewen.com/ |
| http://homebrewlub.us/ | https://tradingvieweu.com/ |
| http://homebrewonline.org/ | https://www.homebrewclubs.org/ |
| http://homebrewupdate.org/ | https://www.homebrewfaq.org/ |
| http://sites-phantom.com/ | https://www.homebrewfaq.us/ |
| http://tradingviewen.com/ | https://www.homebrewonline.org/ |
| http://tradingvieweu.com/ | https://www.homebrewupdate.org/ |
| http://www.homebrewfaq.us/ | https://www.tradingvieweu.com/ |
| http://www.homebrewonline.org/ | https://filmoraus.com/ |
| http://www.tradingviewen.com/ | https://homebrewfaq.org/ |
| https://filmoraus.com/ | https://homebrewfaq.us/ |
| https://homebrewfaq.org/ | https://homebrewlub.us/ |
Ao verificar alguns dos domínios, o BleepingComputer descobriu que, em alguns casos, o tráfego para os sites era direcionado por meio do Google Ads, indicando que o agente da ameaça os promoveu para aparecer nos resultados da Pesquisa Google.
Os sites maliciosos apresentam portais de download convincentes para os aplicativos falsos e instruem os usuários a copiar cacho comando em seu Terminal para instalá-los, o dizem os pesquisadores.
 Adicionado um componente de backdoor ao malware para dar aos operadores recursos de acesso remoto persistente.
Adicionado um componente de backdoor ao malware para dar aos operadores recursos de acesso remoto persistente.
Ladrão de Odisseia, documentado pela CYFIRMA pesquisadores neste verão, é uma família relativamente nova derivada do Poseidon Stealer, que por sua vez foi bifurcado do AMOS.
Ele tem como alvo credenciais e cookies armazenados nos navegadores Chrome, Firefox e Safari, mais de cem extensões de carteira de criptomoedas, dados de chaves e arquivos pessoais e os envia aos invasores no formato ZIP.
É altamente recomendável que os usuários não colem os comandos do Terminal encontrados online se não entenderem completamente o que fazem.
